MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz
Language: English | Size: 3.02 GB | Duration: 9h 10m
TTPs para Ransomware
What you'll learn
Python programming for file manipulation
Cryptography
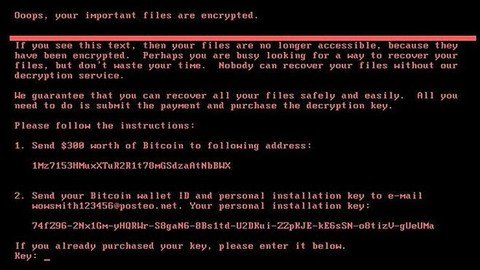
About Ransomware and Notorious Groups
Post exploration basics
phishing
Creating Symmetrical and Hybrid Ransomware
Requirements
There are no requirements for who wants to learn
Description
I had the initiative to create this course to teach a landing on what a real ransomware attack process looks like, using well-known tools used by notorious groups, let's learn about the most famous groups,
accessing sites where stolen data is put for download by several different groups, let's access forums famous for Russian hackers.
After the ransomware and notorious groups history steps, let's go to the more practical step, learning how to create our python scripts, programming logic as an introduction and then, let's start the file manipulation, moving on to AES, RSA encryption, etc. , these classes will help us create our ransomware
let's learn to use tools that are used by these groups, a technique that is becoming very famous, called Living-off-the-Land for dazzling movement
and we are also going to create our own automated tools for mass data theft, ransomware, fake pages for sending emails to download malicious files, using as an example a page created by the North Korean APTs.
The course is still under development and that's why new classes are added every week, classes are in English and there is also subtitles in case you have trouble understanding what I say.
The course is very practical, with windows commands, linux and many concepts in python, don't wait for me to take your hand to guide you, there is Google for that.
Who this course is for
This course is intended for all those who want to learn the basics of the TTPs of a Ransomware attack.
Homepage
https://www.udemy.com/course/techniques-tactics-and-procedures-for-ransomware-attacks/https://hot4share.com/8wjiy6xu1vze/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part1.rar.html
https://hot4share.com/oqg5fiujxm26/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part2.rar.html
https://hot4share.com/74z8ame9f8jr/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part3.rar.html
https://hot4share.com/avm6gqyu8zhe/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part4.rar.html

https://uploadgig.com/file/download/a90E55fbD8cc7cef/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part1.rar
https://uploadgig.com/file/download/0c6E0874405ec60c/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part2.rar
https://uploadgig.com/file/download/5dc050A05cfE2677/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part3.rar
https://uploadgig.com/file/download/7116970866925107/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part4.rar

https://rapidgator.net/file/5266d1eec08735d983c25e66a98d8ba6/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part1.rar.html
https://rapidgator.net/file/2ee305f3e98b621199a1bb6969248c02/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part2.rar.html
https://rapidgator.net/file/f9c0e52109d5007fd54cc879e4163d64/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part3.rar.html
https://rapidgator.net/file/4cc8ee7d4177652c0b4a2ebc2e82927f/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part4.rar.html

https://nitro.download/view/545A617A7790070/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part1.rar
https://nitro.download/view/B6018289BD4767C/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part2.rar
https://nitro.download/view/B73F37181A98437/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part3.rar
https://nitro.download/view/008E7FEA58AA232/w6gda.Techniques.Tactics.and.Procedures.for.Ransomware.Attacks.part4.rar
Links are Interchangeable - No Password - Single Extraction
